We have implemented several changes that will enable you to diagnose and eliminate potential memory leaks more quickly and will make it easier to investigate problems associated with acquiring and releasing licenses.
Search of circular references
The 1C:Enterprise 8 platform uses the object lifetime management strategy that is based on object reference counting. This strategy can be described as follows. Each object of the platform contains a reference count. When a reference to an object appears (when an object is assigned to a variable), the count increases by one, when such reference is removed - the count value decreases by one. When the object reference count equals zero, the object is automatically destroyed, and the memory occupied by it is freed up.One of the peculiarities of object reference counting is the possibility of implementing a circular reference. A circular reference occurs when objects start to refer to each other. For example, if there are objects nested inside other objects, and somewhere deep inside, they refer to the topmost object. The result is a circular reference. In the simplified form, a circular reference can be created as follows:
Data = New Structure;
Data.Insert("Key", Data);
|
If circular references are accumulated during the long period of work, this may result, for example, in the server cluster working process occupying the entire RAM or reaching a restart threshold. Another manifestation of a long-term accumulation of cyclic references can be that session data occupy all the space on the disk that hosts the storage.
We have developed two tools that can help you detect circular references. We recommend using them only during debugging and testing because they require considerable resources, which might adversely affect the execution of 1C:Enterprise operations.
Automatic search of circular references
First of all, we have implemented an automatic search mode for circular references. In this mode, when the platform detects a circular reference, it stops script execution and a dialog box of the following type pops up: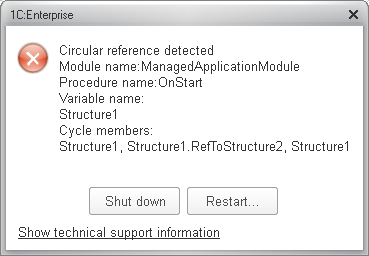
This dialog box lists all the variables, for which circularity is detected. For each variable, all the cycles, in which it participates, are listed (in terms of 1C:Enterprise script).
In this case, the circularity was caused by this script fragment:
Structure1 = New Structure("RefToStructure2");
Structure2 = New Structure("RefToStructure1");
Structure1.RefToStructure2 = Structure2;
Structure2.RefToStructure1 = Structure1;
Structure2 = Undefined;
|
- In the command-line options
- In Designer startup options
- In the conf.cfg configuration file
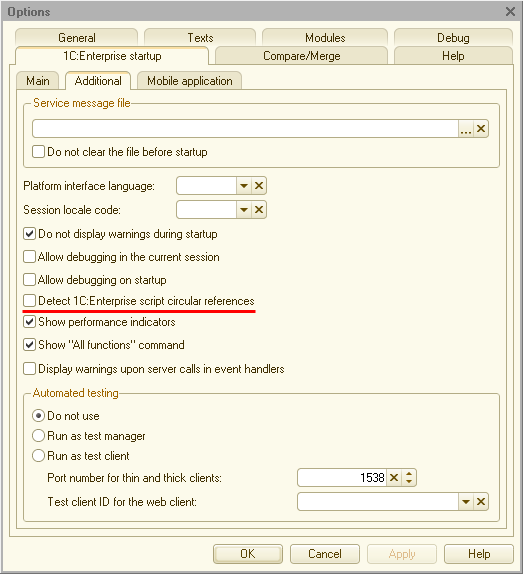
Automatic search mode for circular references can also be enabled in the settings of the technological log. But in this case, script execution will not be stopped, and all circular reference warnings will be collected in the technological log, in the new SCRIPTCIRCREFS event.
Search of circular references from 1C:Enterprise script
For more detailed and accurate diagnostics of circular reference presence, we have implemented a new global context method: CheckScriptCircularRefs(). You can use it to find circular references, for example, whenever you like, or in the procedure of your choice, or to analyze the variable that looks suspicious to you.If you do not specify the parameters of this method, all of the local variables in the stack will be analyzed. If you pass a local variable to the method, only this variable will be analyzed.
Thanks to this method, you receive information similar to that, which results from an automatic search for circular references: names of cyclic variables and a list of cycles for each of them.
Tracking of license acquirement and release
Another group of issues, which were difficult to detect until now, has to do with acquiring and releasing of licenses. For example, if the limit of administrator or developer licenses was suddenly exceeded, the investigation required some significant efforts.We have implemented detailed logging of events related to licensing in the technological log. To this end, we use the LIC event.
Attempts to acquire licenses
Each time the platform attempts to acquire a license, it records the following data: license number, its recipient, whether it is a new license or an old one that is reused, license ID, license type, as well as the license keys and files that were reviewed and on the basis of which the license was acquired.If you use HASP keys, their initialization process is logged. The type of the requested license and a list of available HASP keys are recorded.
Releasing licenses
Every time a license is released, the following data is recorded: license ID, the time when the object of the released license was created, license recipient, license type or key, as well as the number of employed software licenses.Verifying invariability of parameters critical for licensing
We have implemented a periodic (every 20 minutes) verification of the invariability of computer parameters critical for the binding of software licenses. If these parameters undergo a critical change, the event is recorded in the technological log as LIC event. It contains the name of the license file, registration number, PIN code, type of license, the maximum number of users, and the list of critical hardware changes.The first time such change is detected, the 24-hour timeout is set up until the moment when the change is detected by the license binding verification mechanism and when the license file quits working. The system administrator is given 24 hours to fix the issue.




