As we promised in the previous article, we are gradually expanding the functionality of configuration extensions and improving their applicability diagnostics.
Adding roles
In the past, it was possible to change roles of a standard configuration by adopting them and adding to them objects created in the extension. Now you can create roles in extensions.
We can see two major scenarios involving the use of added roles. Firstly, they may be required to create atomic or complex sets of rights to the objects that the extension brings to the configuration (without any binding to the roles existing in the configuration).
Secondly, you can use them to create atomic or complex sets of rights to the configuration objects that take into account specifics of the functionality implemented in extensions.
Roles created in the extensions can be added to users only using 1C:Enterprise script. For example:
CurrentUser = InfoBaseUsers.CurrentUser(); CurrentUser.Roles.Add(Metadata.Roles.ExtAndromedaAdditionalReports); CurrentUser.Write(); |
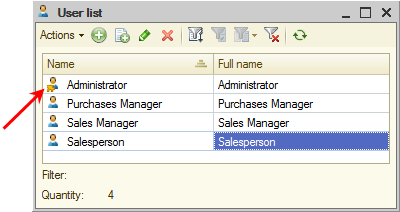
In Designer, you can remove the roles of the user that were added through the extensions. Not one by one, but all together. That is why the user will now have the item titled Roles added by configuration extensions in the Other tab. Clear the checkbox to remove the roles.
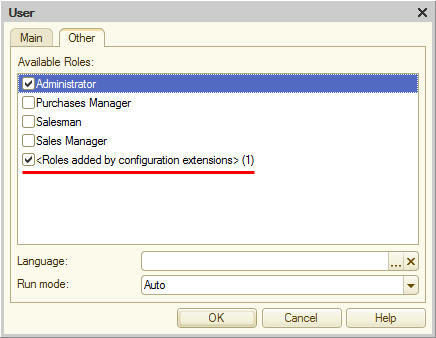
If at some point the extension that added the role ceases to successfully pass the applicability check and becomes inactive, the role that was added from it continues to be available through the UserRoles collection as a usual metadata object. Using 1C:Enterprise script, you can remove it from the user's roles, or add it to the set of roles for another user.
If you delete the extension, all roles that were added by it are also removed from the list of user roles.
Extending configuration roles
Now you can grant or, conversely, deny access privileges for objects in the main configuration in the adopted extension roles.
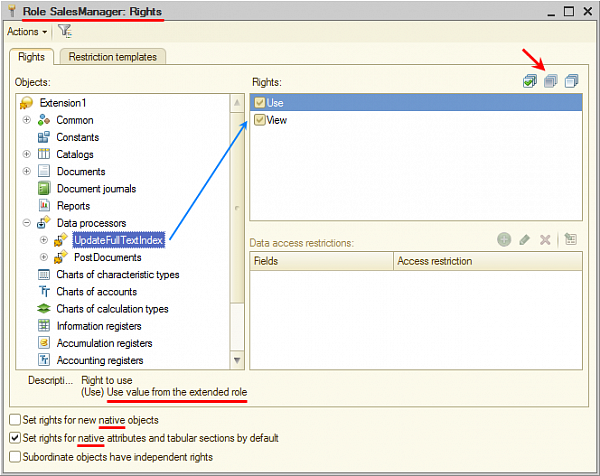
This feature will allow you, firstly, to create complex sets of rights to the objects of configuration and extension, which will take into account the specifics of the extension and will be linked to the roles existing in the configuration.
Secondly, extending configuration roles will reduce the number of rights in configuration roles.
When editing rights to an adopted object, you now have a third option for each checkbox: Use the value from the extended role. All rights to adopted objects have this value by default. We added a button above the list of rights that selects the third option for all checkboxes for an adopted role.
When you edit an adopted role, the word “native” is added to the names of the checkboxes that are located at the bottom of the window:
- Set rights for new native objects
- Set rights for native attributes and tabular sections by default
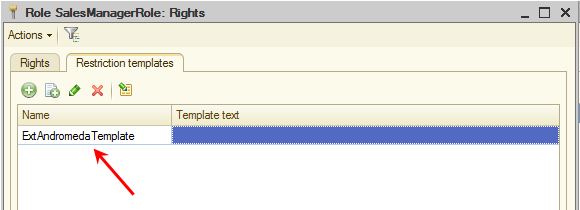
Restrictions of native and adopted roles
Native roles of extensions have a number of restrictions. First of all, there are "constructive" restrictions, which means that these roles cannot provide a user with the rights available for the root element of the configuration.
On the other hand, native roles of the extension can be restricted by cluster security profile settings. We believe that this feature will be in demand in the configurations that work in SaaS mode. With its help, you can create a role that gives the user access to all the configuration objects, with the exception of those that are responsible for service and administrative functions. Then you use this role to restrict extending access rights for the safe mode security profile and for the profiles assigned to specific extensions.
If such a role is not available, you can implement the restriction as a list of roles that provide access to secure (from the service point of view) objects.
In order to implement these features, we have added an access rights extension checkbox to the security profile, to the Grant full access to a group. We have also added the Roles that restrict the extension of the access rights field. You can use this field to specify the list of roles separated by ";".
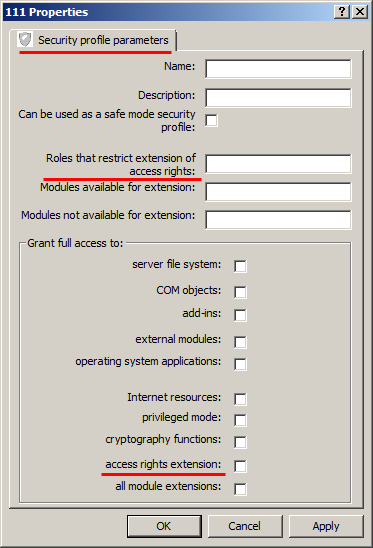
If a profile is in effect while the extension is running, the platform interprets the new parameters as follows.
If the field value is specified, the role that is changed or added by the extension provides only those access rights to configuration objects that are provided by at least one of the roles specified in the field.
If the field value is not specified and the full access checkbox is not selected, rights to configuration objects are not extended. You still have the option to deny some rights to the objects.
If it turns out that, upon extension startup, the security profile restricts the provision of a certain right to a certain role included in the extension, the user will receive the following message: "SomeRight right to SomeObject object for SomeRole role is restricted by the security profile”.
Applicability сheck
A certain extension cannot always be applied to a specific configuration. For example, because it has errors in its modules. Or because the properties of adopted objects with value check enabled do not match.
The first problem can be solved easily before startup using extension module verification. The second issue, however, can only become known to you after you run the application when the platform attempts to apply for the extension. If there is something wrong with the objects accessed by the extension, the platform reports it and does not apply for the extension.
In order to minimize the complexity of the extension development process, we analyzed the situation, slightly changed the behavior of the system, and implemented a number of verifications.
Now, new diagnostic tools allow you to check the applicability of extensions before their actual startup together with the configuration.
When you run the client application
The behavior is changed in the way that now when you run the client application, previous messages about extension applicability issues are no longer displayed. In the new version, if any errors are detected when an extension is applied at startup, the platform displays a popup notification window with a hyperlink.
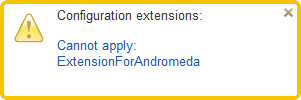
Clicking the hyperlink opens the Information for the technical support window. All messages about occurred errors are now added to this window, which can also be opened from the About 1C:Enterprise dialog box.
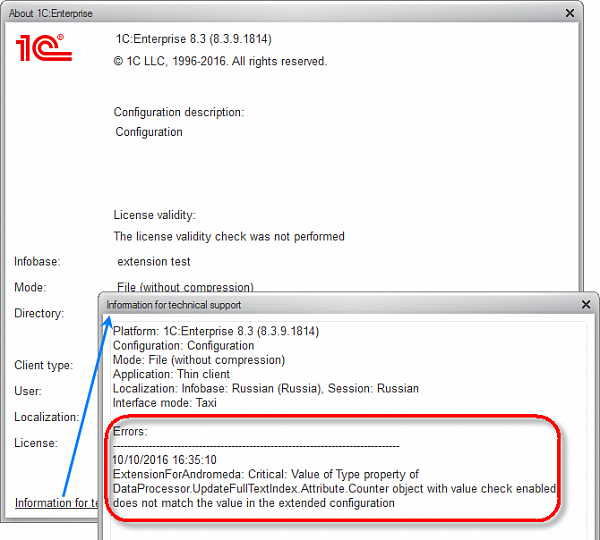
All of these errors can now be detected beforehand in different places.
In Designer
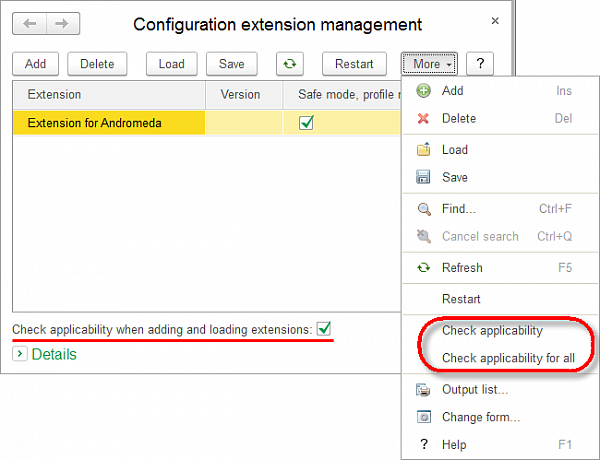
Diagnostics are first of all available in Designer. We have added two new commands in the Configuration extensions window: Check applicability and Check applicability for all.
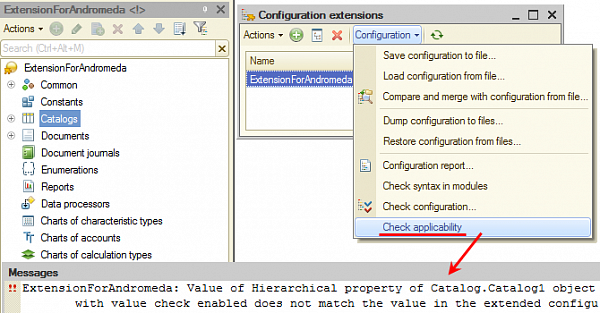
These commands check the applicability of the selected extension (or all extensions) in regards to a specific infobase. This verification takes into account even the changes in the extensions and configuration that have been made but not applied to the infobase.
You can run a similar verification also in the Designer batch mode. For this purpose, we have added a new command-line option /CheckCanApplyConfigurationExtensions.
In 1C:Enterprise script
Diagnostics are also available in 1C:Enterprise script. We have added a new method CheckCanApplyAll() to the ConfigurationExtensionsMananger. And to the ConfigurationExtension object, we have added the CheckCanApply() method. You can use these methods to check the applicability of all (or one) extensions of the infobase in the current data area in accordance with the load order and taking into account the extensions that were already verified.
An important and interesting feature here is that the CheckCanApply() method allows you to check the applicability of a new version of the extension before it is loaded directly into the infobase. You can pass a new version of the extension to this method as binary data.
In “Manage configuration extensions” standard data processor
And finally, the last place where you can find the new diagnostics tools is Manage configuration extensions. We have added the Check applicability when adding or loading the extensions checkbox. If it is selected - which it is, by default - applicability will be checked before an extension is added or loaded.
We have also added two commands that allow you to check the applicability of those extensions that are already available in the list to the More menu.