At users’ request, version 8.3.27 of the platform introduces a new method of authentication: email-based authentication.
How It Works
When properly configured, the user’s authentication window includes an option called Email-Based Authentication:
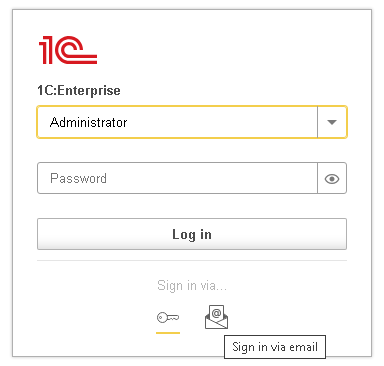
1. When the user selects this option, they are prompted to enter their email address.
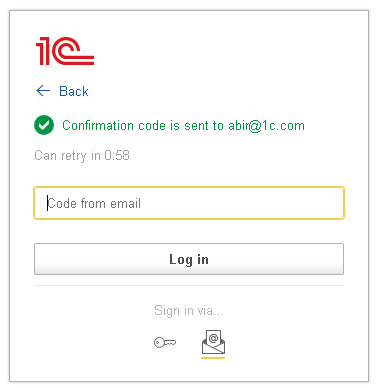
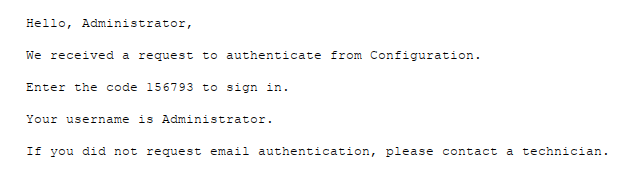
2. If the address matches the email address specified for the user in the infobase, a login code is sent to that address.
3. The user then enters this code to access the infobase.
How to Set It Up
To enable email-based authentication:
1. Activate this feature for the infobase
-
In Designer mode, go to Administration > Additional Authentication Settings, or
-
In 1C:Enterprise mode, go to Functions for Technician > Additional Authentication Settings.
2. Specify the mail service to use
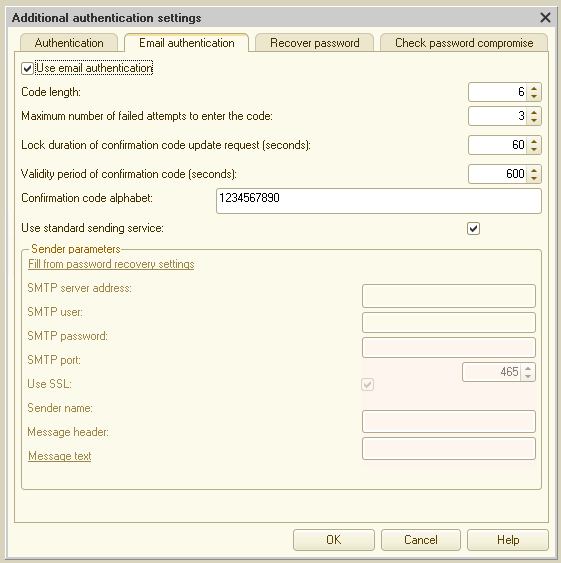
3. Configure the Confirmation Code Alphabet
-
In the same settings window, you can define the characters used to create the random code sent to users.
-
For example, if you set the alphabet to "abcdefghijklmnopqrstuvwxyz1234567890", the user’s code is randomly generated from these letters and digits.
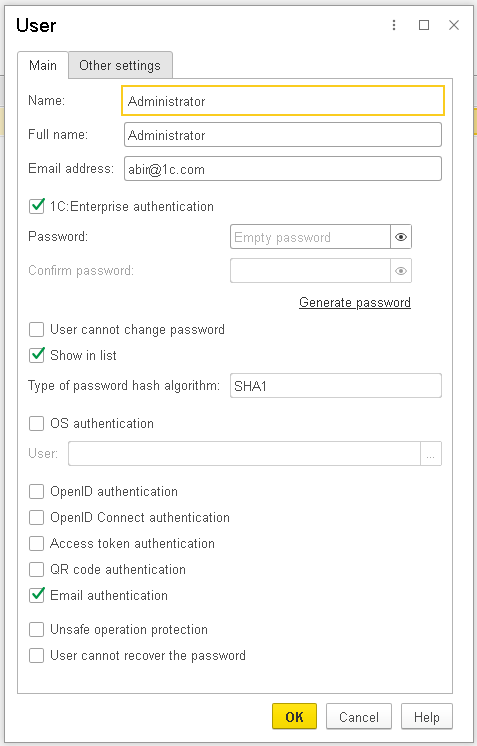
Additionally, each user must have Email-Based Authentication enabled in their settings.
The 1C:Enterprise language has been extended to support this new type of authentication.
Usage Scenarios
Email-based authentication offers new, secure, and convenient login scenarios for both administrators and users. For example:
Granting Access Without an Explicit Password
You can allow a user to access the infobase without sending them a password in plain text.
First-Time Login Flow
1. The user receives a login for future sessions and a link that allows them to sign in via their email address.
2. After email-based authentication, an application form is displayed, prompting the user to set their password immediately.
This approach ensures that passwords are not shared in plain text and gives administrators tighter control over how and when users set up their credentials.




