Event Log Analyzer
- Reports on user activities, duration of scheduled jobs, and log records of critical importance.
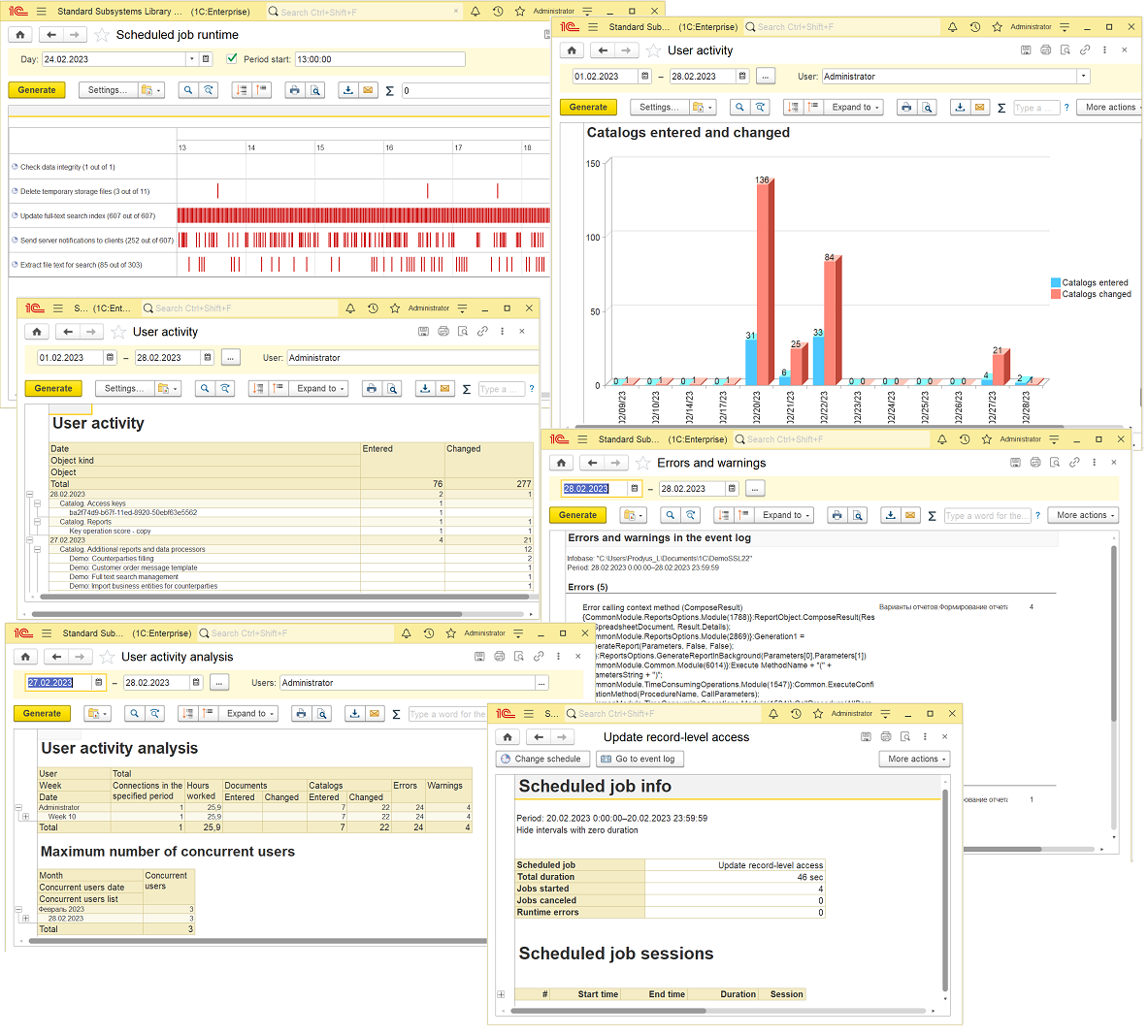
- Allows applications to attach additional (external) reports and data processors without modifying the configuration.
- Additional reports and data processors can be linked to specific types of objects or sections of the command interface.
- Data processor activation on schedule.
- Management of additional reports and data processor lists via dedicated administration tools.
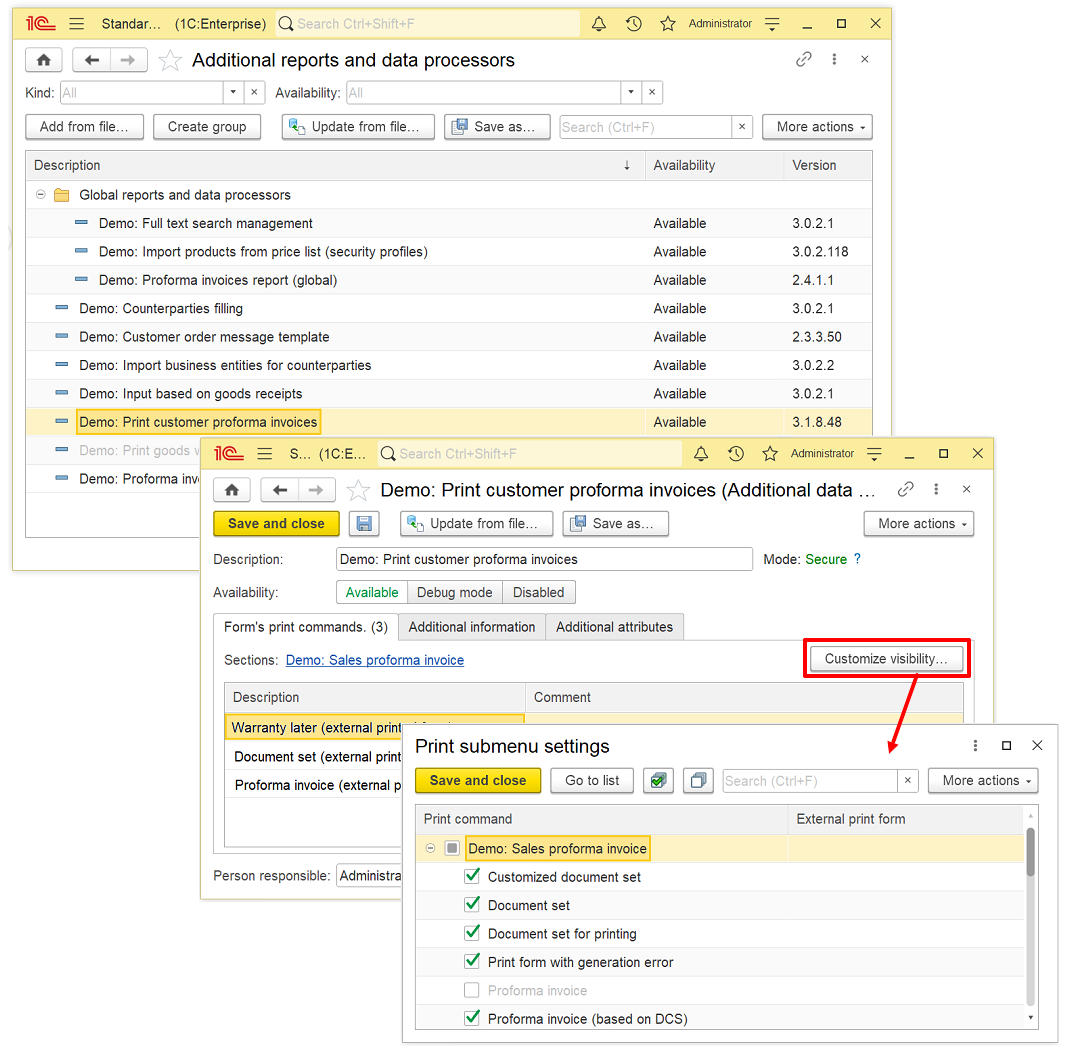
- Ready-to-use workstations (panels) in the Administration section.
- Administration panel layout gets adjusted to the currently selected mode in an application.
- Automatic update to a new version of an application, installation of error-correcting patches on demand (at a specified time in the future or on the application closing).
- Installation of updates from a specified file on a local or network drive.
- Changes in the main configuration apply to the database configuration.
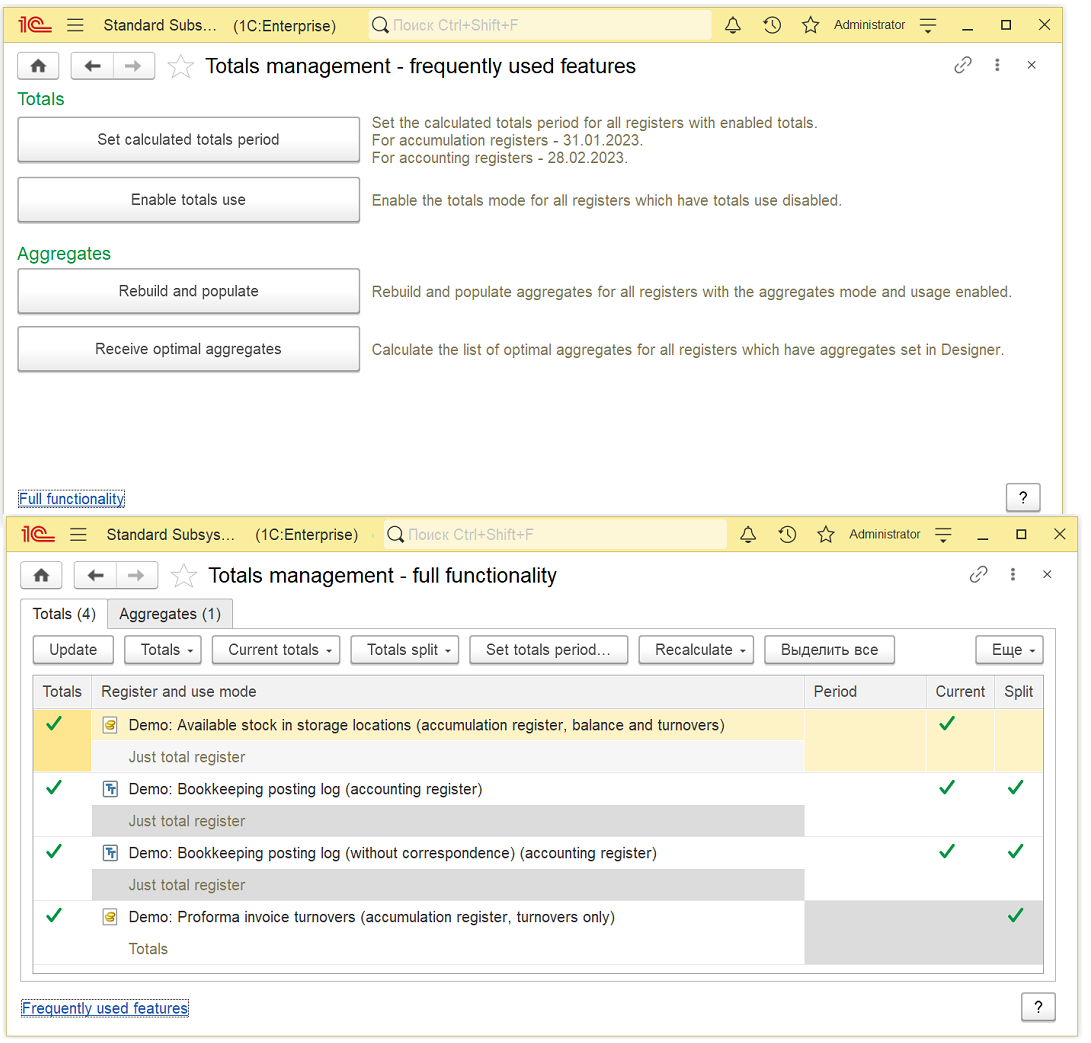
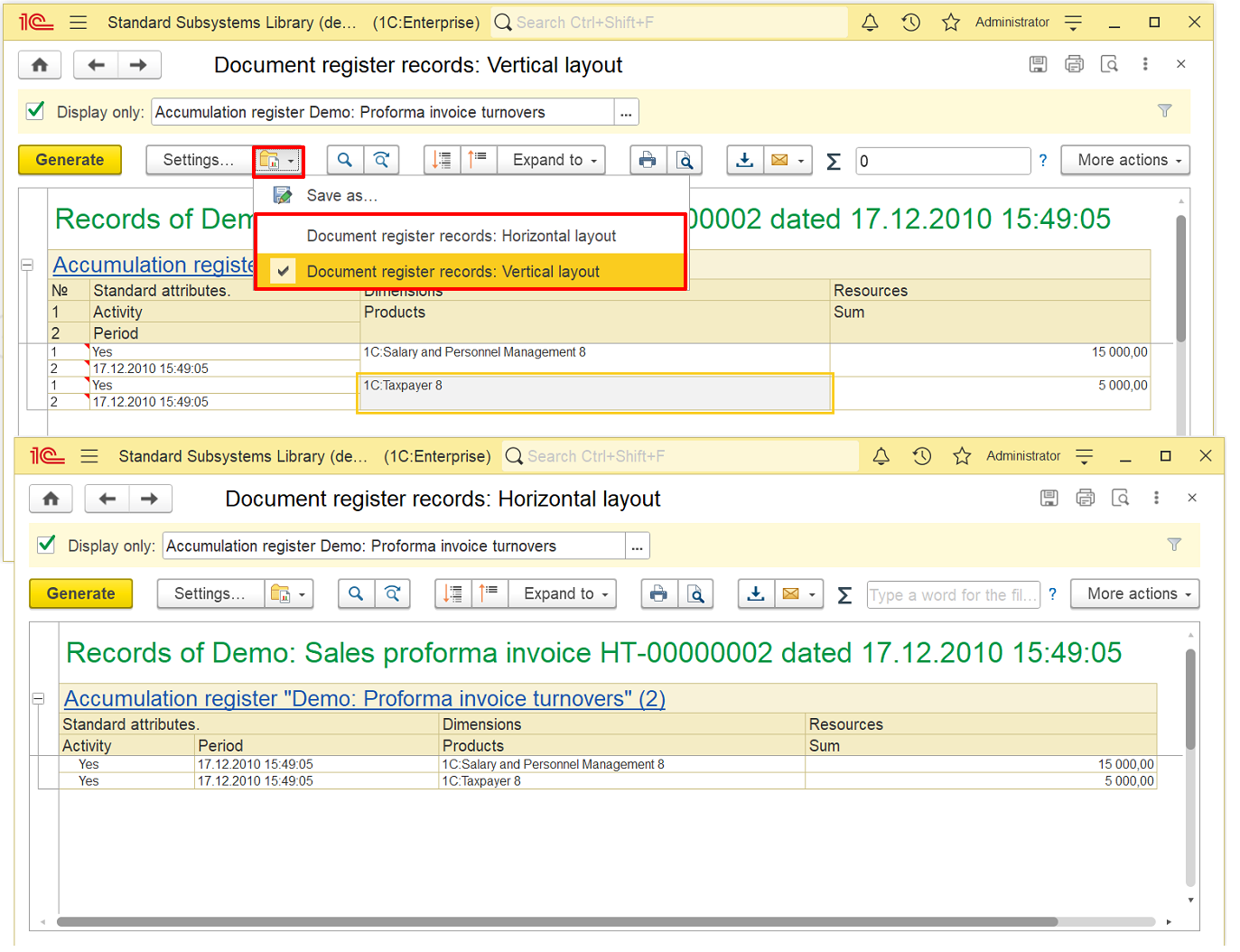
- The report provides information on records generated by posting documents and the registers that received such records.
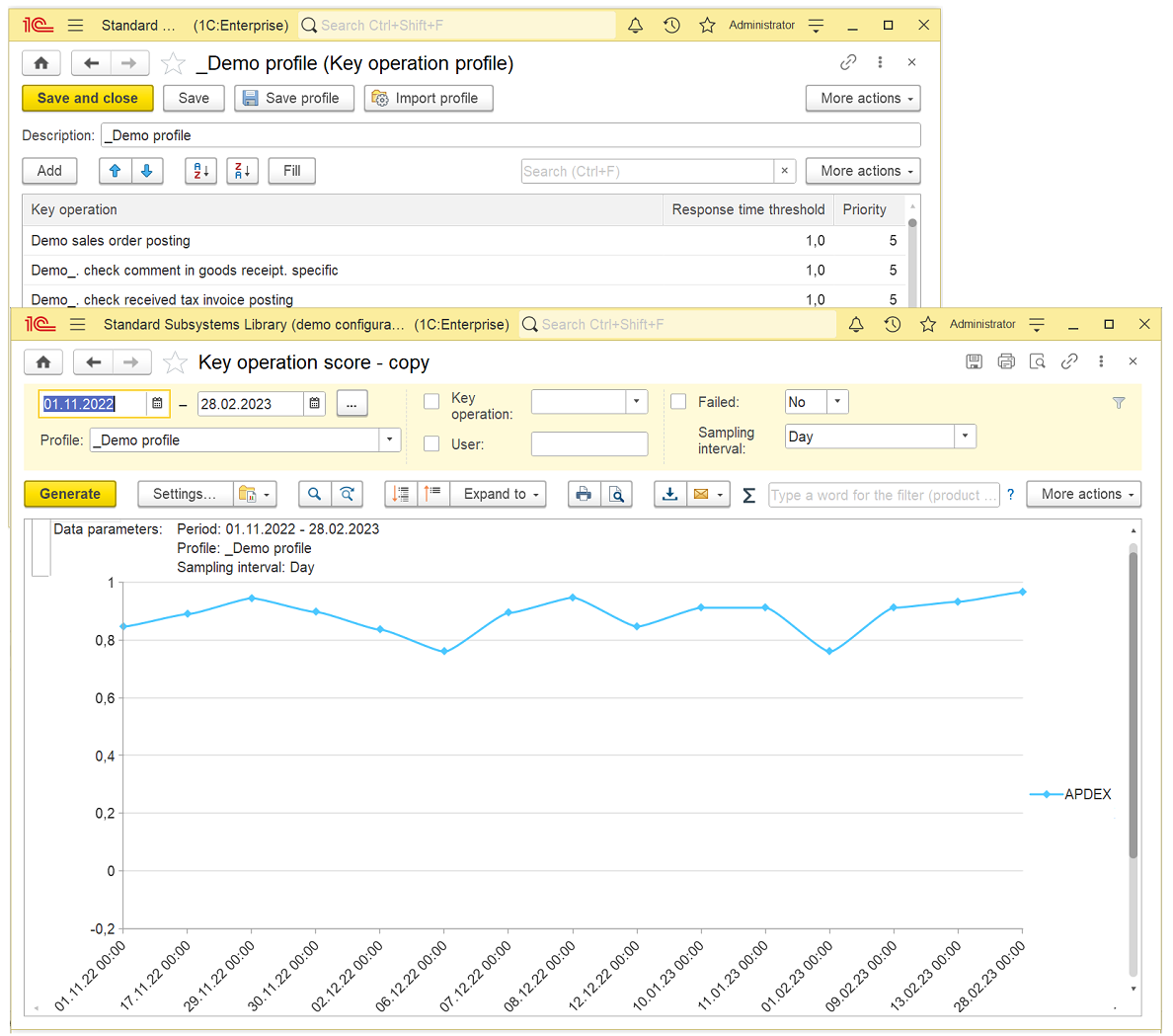
- Benchmarking of application’s integral performance with the Apdex method.
- Simplified and automated collection of data regarding the time spent on each key operation.
- Tools for analyzing the measurement results.
- Automatic export of performance indicators.
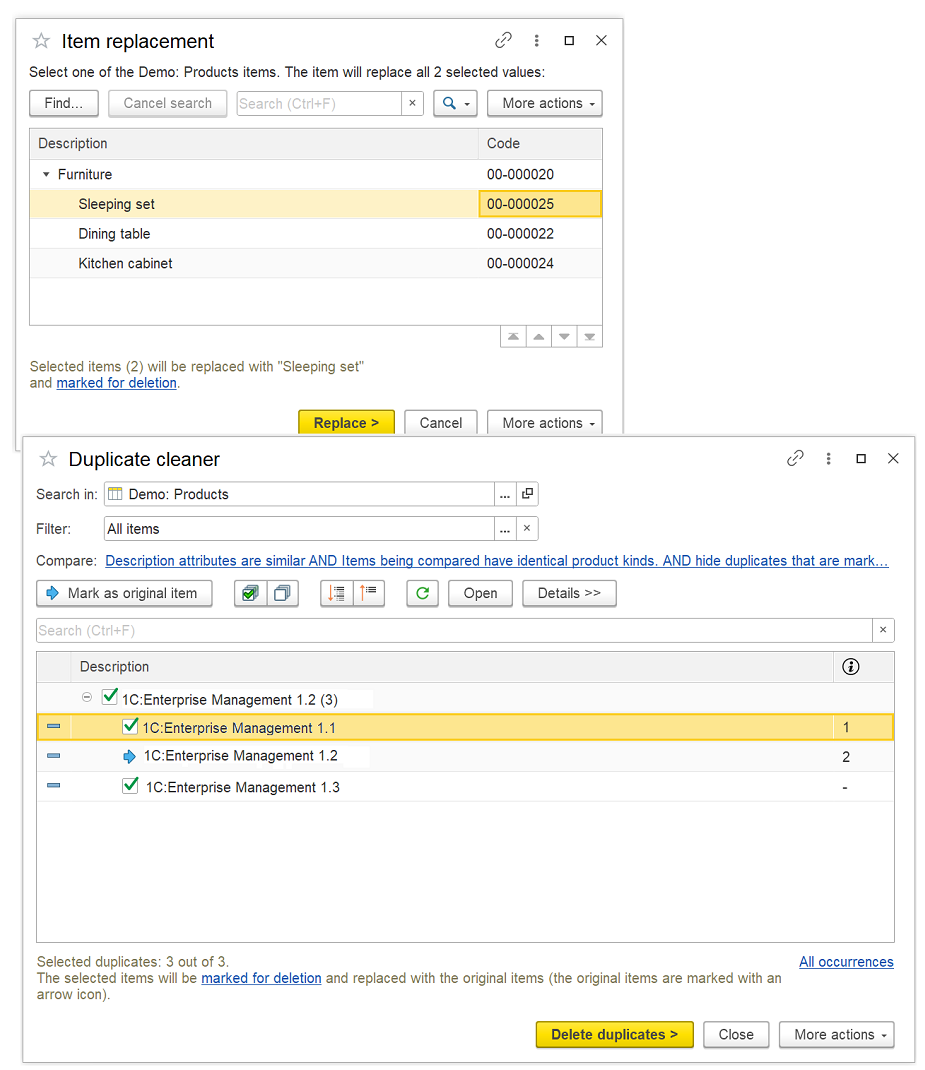
Duplicate Objects Detection
- Search and removal of duplicate catalog elements.
- Replacement of one element with another, merging of several identical list elements into one.
- Automatic replacement of links to the removed duplicates in all documents and lists of an application.
- Report on where a specific element is used.
- Automatic configuration of infobase security profiles.
- Access to report on attached external resources.
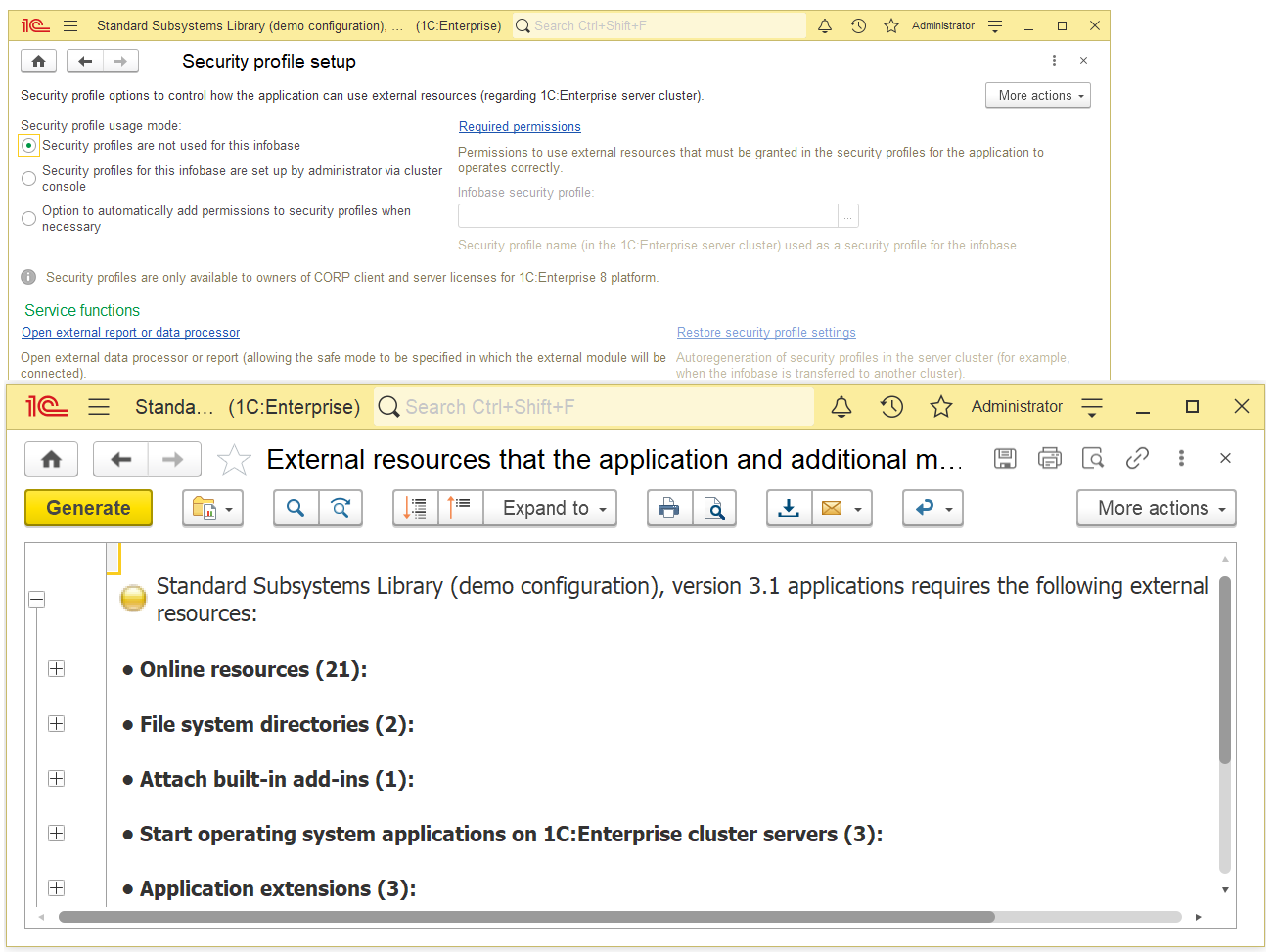
- The list of scheduled jobs with customizable parameters (schedule, job start and stop).
- External resources (data synchronization, mail send/receive, etc.) get locked at the start of infobase copying process.
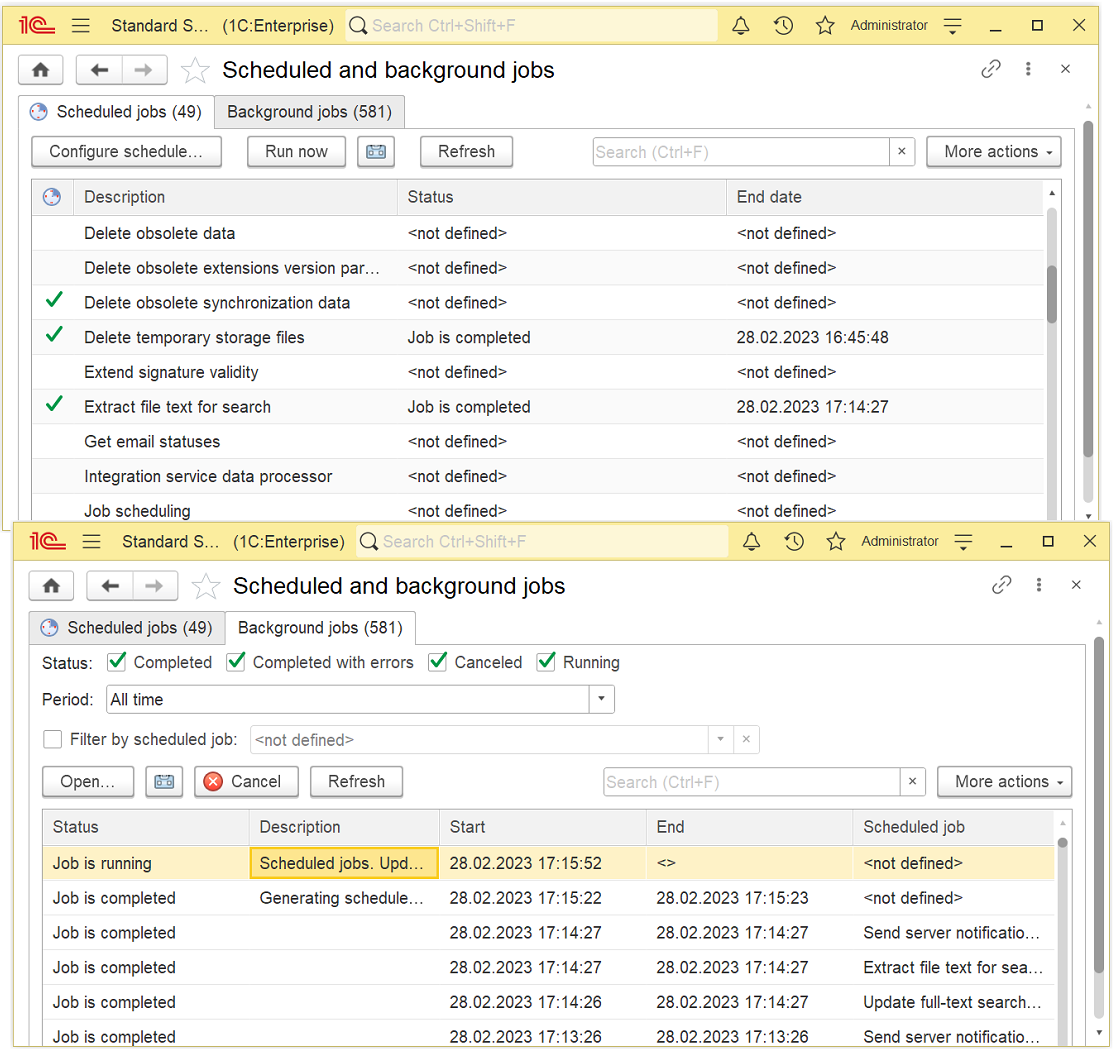
- Creation of information database backup copies on demand or according to a schedule.
- Recovery of infobase copies from backup.
- Reminding to configure backup settings (also in client-server mode).
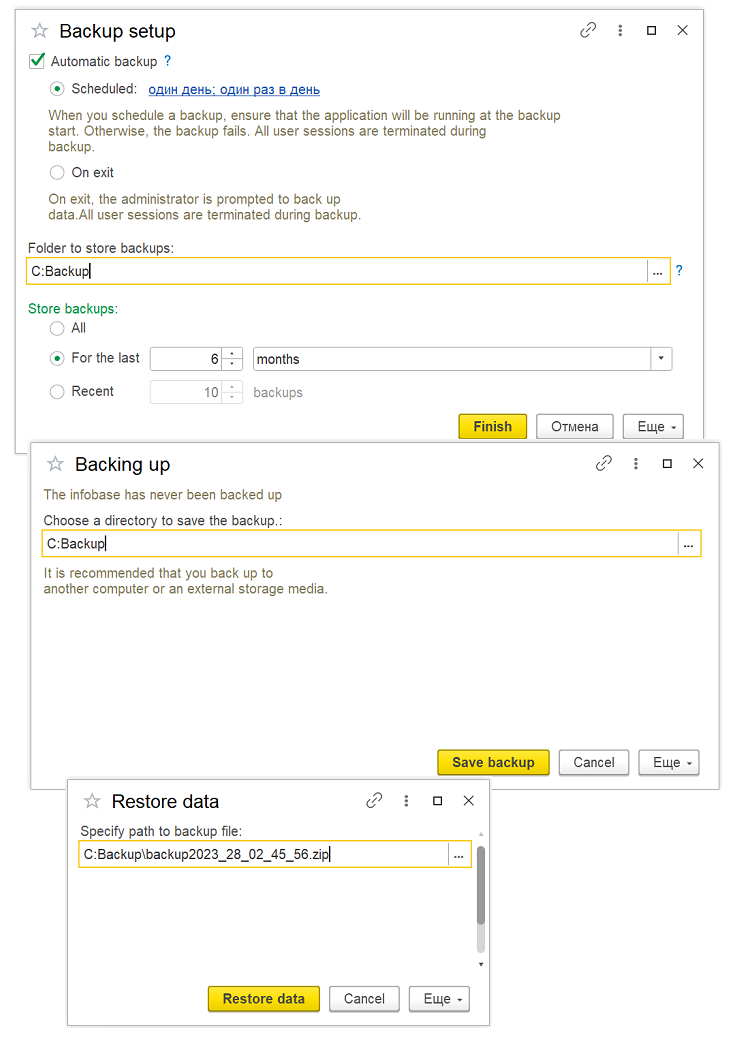
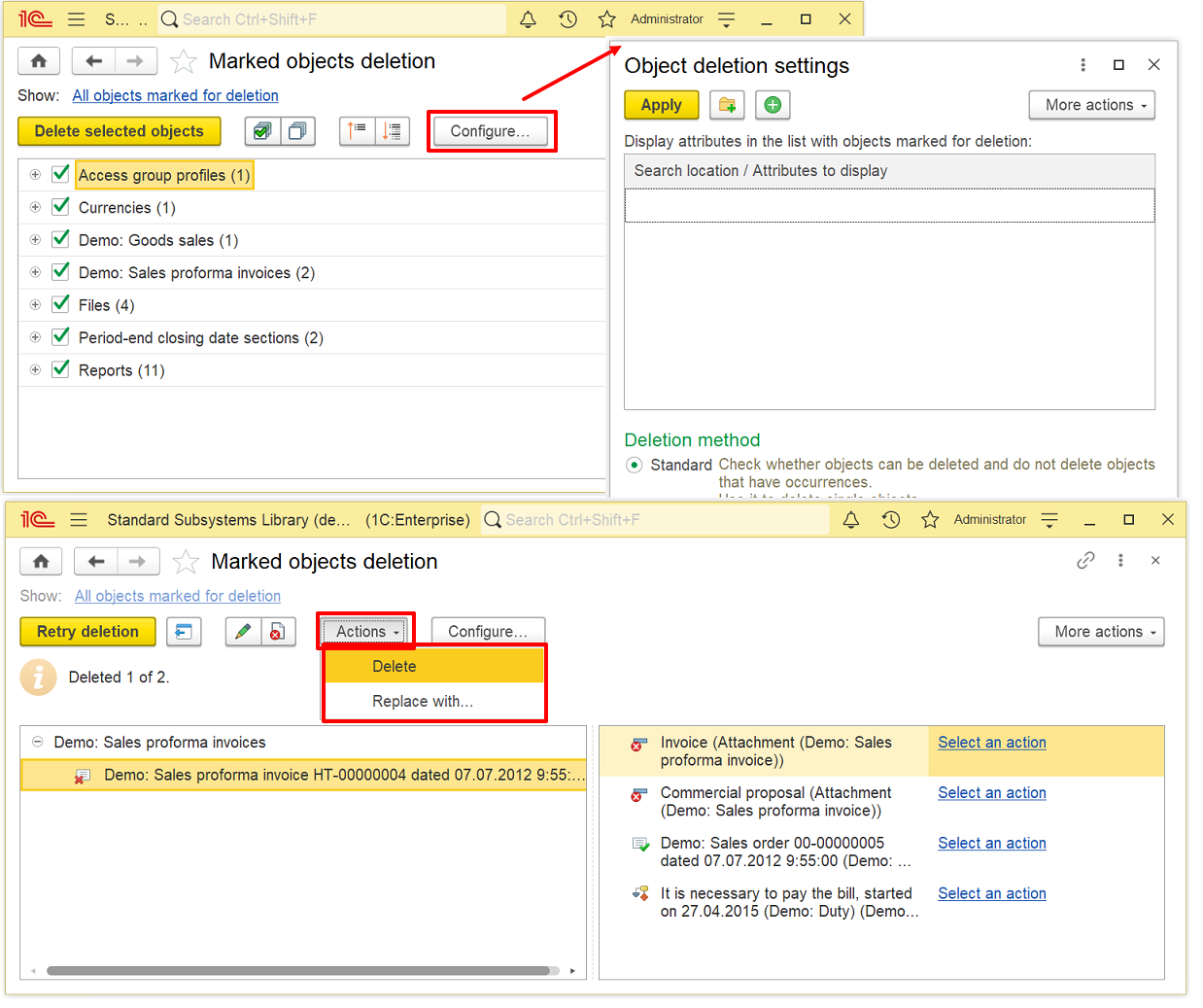
Marked Object Deletion
- Deletion of marked objects with subsequent control of integrity (checks if other objects refer to deleted ones).
- Scheduled deletion of objects in the background.
- Option to hide objects marked for deletion.
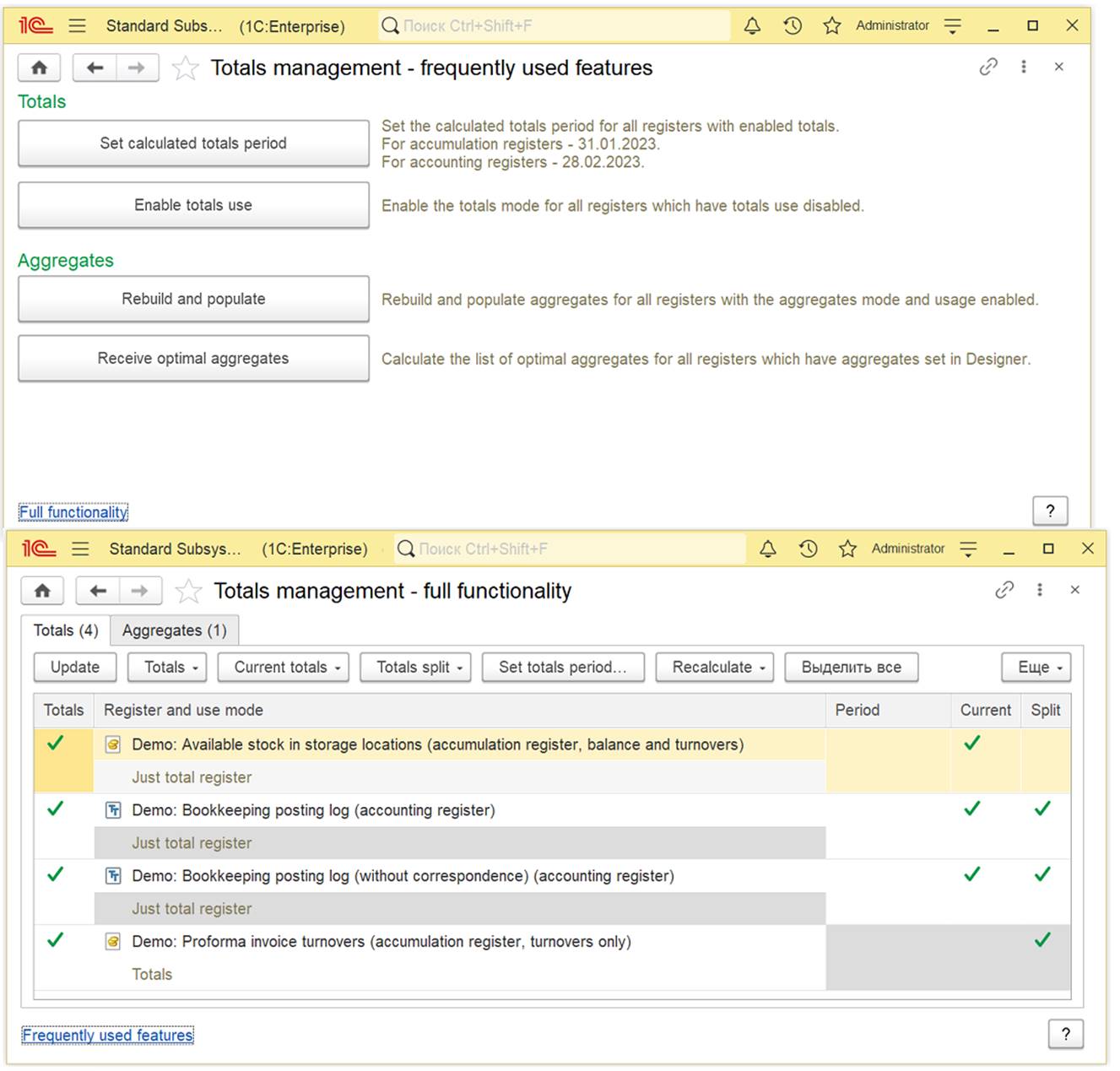
- Administration of totals and aggregates in turnover accumulation registers.
- Scheduled moving of totals border, recalculation, and updating of aggregates (according to the schedule).
Next page: Service Subsystems
Get more details: Downloads
 Desktop version
Desktop version