1C:Enterprise Infobase in IIS: HTTP vs HTTPS
If you run a 1C:Enterprise Infobase in Microsoft Internet Information Services (IIS), you probably published it with default settings: via HTTP protocol only.
To secure external connections to the Infobase, you might want to encrypt them via HTTPS protocol.
To do this, you need to install an appropriate TLS certificate to IIS and ensure that your IIS server requires HTTPS connections.
The rest of the article assumes that you already have your 1C:Enterprise Infobase published via HTTP in IIS.
When choosing a TLS certificate to use, you have the following major options:
-
A certificate issued by an authorized center.
This is a universal option. It provides better confidence for external users that connect to your IIS server. This happens because sites whose certificates are issued by trusted authorities like VeriSign, Thawte, Comodo, Semantec, and others are opened without any warnings in your users' web browsers.
-
A self-signed certificate.
This means that it is you who issued the certificate for your server.
This option is the simplest one because here there is nothing to pay for. Though, by default, web browsers treat a site with such a certificate as not trusted and warn your users about this. To view the contents of such a site, each user has to add the site to the exceptional list of the sites to be trusted. That's why this option is better for situations where users access your IIS server via your local network.
Note No matter which certificate option you choose, we highly recommend you to use TLS certificates instead of SSL ones, because the security level the SSL certificates provide is not sufficient now.
Installing authority center's TLS certificates to IIS
In this example, we will use the "letsencrypt-win-simple" application, which automatically:
- makes the Let's Encrypt authority center issue an appropriate TLS certificate
- installs the certificate to your computer
- binds the certificate to your IIS server's 443 TCP port
As you can see, this greatly simplifies the configuration procedure. Of course, you can purchase a certificate in an authority center in a traditional manner and install it manually.
To install authority center's TLS certificate to IIS:
-
Ensure you have a registered domain name.
Say, "cfg.cf".
-
For the server where you have IIS installed, open and forward its 443 TCP port.
-
From https://github.com/Lone-Coder/letsencrypt-win-simple/releases, download "letsencrypt-win-simple" application's installation package.
-
Extract the entire package to a folder and then execute the letsencrypt.exe file on behalf of the local administrator.
The application runs in the console window.
-
In the console window, type your email address and press ENTER.
-
Type "Y" and then press ENTER.
The application searches for DNS records in your IIS server and displays found records.
-
Type the number that corresponds to the domain you are configuring ("cfg.cf") and then press ENTER.
-
Wait for the confirmation that the TLS certificate is ready and installed in IIS, and then close the "letsencrypt-win-simple" application's window.
-
Run IIS Manager.
-
In the connections tree, expand components, right-click "Sites > Default Web Site", and then click Bindings.
-
In the Site bindings table, select the appropriate row for port 443 and click Edit.
-
Check whether your domain name and certificate are bound to the port.
-
Open 1C:Enterprise.
-
Select your Infobase and click Designer.
-
Log on to the Infobase as Administrator.
-
From the Administration menu, select Publish to web-server.
-
Make sure you have the checkboxes selected as illustrated in the figure below.
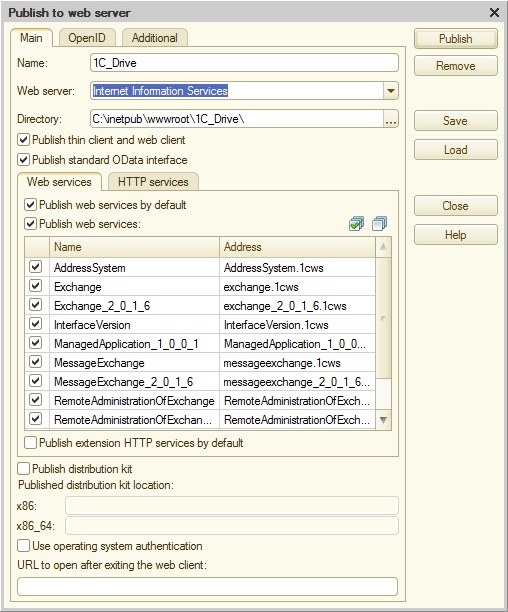
-
Click Publish.
The system displays the message box that informs you that the publication is finished.
-
In the message box, click OK.
The system displays the message box that asks you whether you want to restart the web-server.
-
In the message box, click Yes.
Now you have your 1C:Enterprise Infobase re-published with the HTTPS support. Let's check how it works.
-
Check whether your IIS server is accessible via HTTPS protocol ("https://cfg.cf") from an external network.
For instance, via the Opera web browser with the VPN support.
-
In the web browser, check the contents of the TLS certificate (validity, supported encryption, domain, and so on).
Note The certificate is valid for 365 days.
Now you have your IIS server with your 1C:Enterprise Infobase published via HTTPS protocol with the authority center's TLS certificate applied.
Installing self-signed TLS certificates to IIS
Depending on the operating system you use, there are different tools you can use to create self-issued TLS certificates.
For example, on Windows, these tools are as follows:
- MakeCert. For more information, see https://msdn.microsoft.com/en-us/library/windows/desktop/aa386968(v=vs.85).aspx. Note that Microsoft marks the tool as deprecated.
- New-SelfSignedCertificate. For more information, see https://technet.microsoft.com/library/hh848633.
- New-SelfSignedCertificateEx. For more information, see https://www.sysadmins.lv/projects/pspki/new-selfsignedcertificateex.aspx.
Although their syntax is different, the purpose of their main parameters is the same:
- "CN" ("Common Name") is for your server's domain name. Say, "cfg.cf".
- "DNS name" (if the tool supports it) is also for your server's domain name.
- "O" ("Organization") is for your company's legal name.
For instance, the following command creates a TLS certificate for the "cfg.cf" domain and places it to the list of personal certificates on your computer:
New-SelfSignedCertificate -DnsName "cfg.cf" -CertStoreLocation cert:\LocalMachine\My
To install a self-signed certificate to IIS:
-
Ensure you have a registered domain name.
Say, "cfg.cf".
-
For the server where you have IIS installed, open and forward its 443 TCP port.
-
By using a tool of your choice, create a self-signed personal certificate for your domain name and your organization.
-
In the command line, run the "certmgr.msc" command and check whether the list of personal certificates contains the newly created certificate.
Note The certificate is valid during 365 days.
-
Export the certificate to an external file in DER encoded binary X.509 (.CER) format.
For more information, refer to https://technet.microsoft.com/en-us/library/cc730988(v=ws.11).aspx.
-
Import the certificate from the file to the Trusted Root Certification Authorities certificate store.
For more information, refer to https://technet.microsoft.com/en-us/library/cc754489(v=ws.11).aspx and https://technet.microsoft.com/en-us/library/cc732443(v=ws.11).aspx.
For instance, the following command imports the certificate from the "C:\certs\cfg_cf.cer" file to the Trusted Root Certification Authorities certificate store:
certutil -addstore "Root" "c:\certs\cfg_cf.cer" -
Run IIS Manager.
-
In the connections tree, expand components, right-click "Sites > Default Web Site", and then click Server Certificates.
-
Specify the self-signed certificate as your server's certificate.
-
In the Site bindings table, click Add.
-
In the dialog, select the "https" type, port 443, your domain name, and the server certificate and then click OK.
-
Open 1C:Enterprise.
-
Select your Infobase and click Designer.
-
Log on to the Infobase as Administrator.
-
From the Administration menu, select Publish to web-server.
-
Make sure you have the checkboxes selected as illustrated in the figure below.

-
Click Publish.
The system displays the message box that informs you that the publication is finished.
-
In the message box, click OK.
The system displays the message box that asks you whether you want to restart the web-server.
-
In the message box, click Yes.
Now you have your 1C:Enterprise Infobase re-published with the HTTPS support. Let's check how it works.
-
Check whether your IIS server is accessible via HTTPS protocol ("https://cfg.cf") from an external network.
For instance, via the Opera web browser with the VPN support.
The web browser might warn you that the certificate is not trusted. This happens if you access your site not from the computer where you have IIS installed.
-
In the web browser, click Continue to this website (not recommended).
To avoid displaying such a message, ensure that the server's certificate belongs the Trusted Root Certification Authorities certificate store on each computer from which you are going to access your site. For instance, to each computer in your domain. To automate such a configuration, you can rely on Windows Group Policy Object (GPO).
-
In the web browser, check the contents of the TLS certificate (validity, supported encryption, domain, and so on).
Now you have your IIS server with your 1C:Enterprise Infobase published via HTTPS protocol with the self-signed TLS certificate applied.
Next page: Dump generation at unexpected application shutdown on Linux

